Websites are vulnerable to assaults such as hacking, defacing, crypto-jacking, and others. An average web attack occurs every 39 seconds. According to research from the Clark School at the University of Maryland. This shows that security experts should view web security As a crucial component in preventing cyber attackers from accessing sensitive data. Most often, phishing, one of the social engineering assaults, is the first step in these attacks, which typically followed by malware, ransomware, credential stuffing, and other cyberattacks.
The security team must immediately give ordinary staff the necessary security knowledge and training to reduce the risk of social engineering attacks. Meanwhile, It then followed by hacks such as credential stuffing, malware, and ransomware. After that, The security team must immediately give ordinary staff the necessary security knowledge and training to reduce the risk of social engineering attacks.
Describe web security
Automated software and tools are used by cybercriminals to find vulnerable websites. They then execute an assault to take advantage of the vulnerabilities found in an effort to access private information. Web security encompasses a variety of techniques and technologies. Involvement from security experts in order to prevent offenders from accessing the websites by locating and fixing the flaws.
The need for web security: why?
Web security shields companies from financial loss maintain the value of their reputation and prevent unintentional website closure. Therefore, A web attack may cause a website to crash or respond slowly. Which would be extremely detrimental to the company. As a result, Security experts can assist the firm in expanding without disruption or loss due to information security breaches with the right web security plan.
These helpful hints will help keep a website safe from intruders. That is to say, The security and network administrators of a company or an ISP could also implement some of these measures to safeguard their users.
1. Make use of a reliable web browser
Popular web browsers like Google Chrome, Mozilla Firefox, and Windows Internet Explorer/Edge all offer frequently updated web security features that can help you avoid harmful URLs. In other words, Keep your web browser in automatic update mode or make regular updates.
2. The privacy and security settings of your web browser
To safeguard your identity and prevent a data breach, you must maintain the privacy and web security settings in your browser. For example, send a “Do Not Track” request along with your browsing activity. You can also turn off the webcam or microphone to prevent nefarious programs and websites from using it.
3. Avoid using short URLs
One of the primary strategies attackers employ to conceal and alter harmful URLs is the use of shortened URLs. Above all, It is particularly challenging for their targets to predict where a short URL will take them when they click on one. Unlike hyperlinks, short URLs can display the same link address even when your mouse hovers over the link. It is therefore difficult to tell whether it is a phishing attempt or a cyber prank because it would likely navigate to a bogus website.
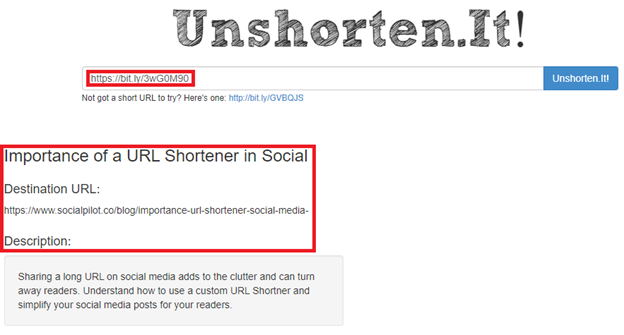
4. HTTPS URLs are superior to HTTP URLs
You might have observed that the URLs of certain websites begin with HTTP, while those of others begin with HTTPS, the latter of which is actually HTTP with encryption, i.e., secured. Most importantly, The TLS (SSL certificate) used by the HTTPS protocol to encrypt standard HTTP requests and responses improves web security over HTTP. Therefore, it is advisable to only click on links and websites that are encrypted (HTTPS).
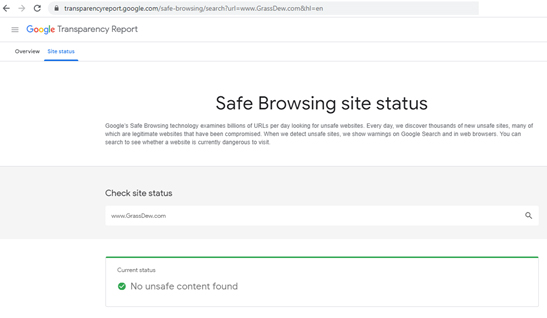
5. Verify a site’s Google Safe Browsing status
As was already noted, numerous browsers have different web security capabilities. Certainly, One of the most well-known is Google’s Safe Browsing technology, which scans billions of URLs daily in an effort to identify potentially dangerous websites. Meanwhile, By using this technique, thousands of new hazardous websites are found every day, many of which are trustworthy websites that have been compromised. Similarly, They display warnings on Google Search and in computer browsers when they find hazardous sites. At https://transparencyreport.google.com/safe-browsing/search?hl=en, the Google transparency report application allows you to do a search to determine whether a website is now risky to access.
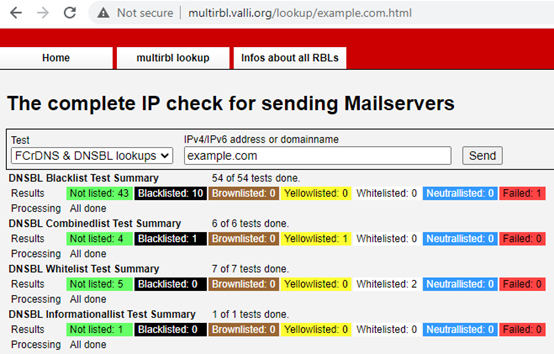
6. Verify whether the website’s IP address is blacklisted
There are further internet resources that enable us to see if the IP address of a website is included in the Global Blacklist Database. Multiball, a free web application that searches various DNS BlackLists (also known as RBLs or DNSBLs), is one of these well-liked tools. http://multirbl.valli.org/
7. Verify a website’s standing
A number of internet services run the website through various blacklist engines and analyze its online reputation using various methods to make it easier to find hazardous and fraudulent websites. It enables you to quickly identify websites that are engaged in malicious or fraudulent activity. Above all, This procedure also aids in determining whether a specific website is a phishing website or not.
Some popular online tools are listed below:
- Norton safe web (https://safeweb.norton.com)
- TrendMicro Site safety (https://global.sitesafety.trendmicro.com/index.php)
- mxtoolbox (https://mxtoolbox.com/)
- urlvoid (https://www.urlvoid.com/)
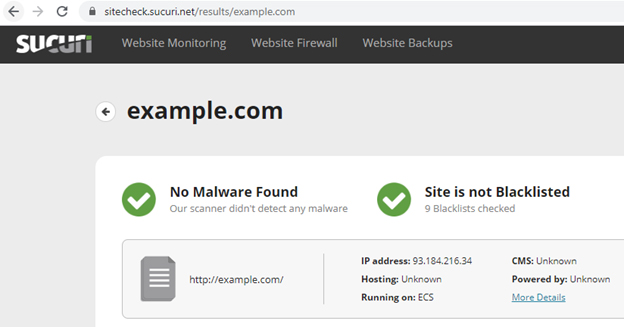
8. Recognize the origin of the website’s URL
Various website scanners assist in checking a website for any dangerous code, viruses, out-of-date software, known malware, blacklisting status, and website faults. Certainly, You may learn more about any website using one of the many website scanners available.
- Website virus scanner available at Web Inspector (https://webinspector.com)
- (https://sitecheck.sucuri.net) Sucuri
- (https://scanner.pcrisk.com) PCrisk
9. Develop the practice of never clicking an unknown URL directly
For instance, if you receive a URL that is highly known to you, copy it and paste it into the browser. Similarly, you can choose not to click and have the URL open in the device’s default browser by doing nothing. As a result, typing it into a web browser is preferable. That is to say, It lessens the chance of falling into online scams.
10. Support the reporting of harmful websites
You can notify the few services listed below about the harmful URL. That is to say, They will analyze your reporting more, which will be beneficial to many.
- Fortinet (https://www.fortinet.com/)
- Sophos (https://www.sophos.com/en-us.aspx)
- Trustwave (https://www.trustwave.com/en-us/)
- Bitdefender (https://www.bitdefender.com/solutions/trafficlight.html)
- Norton (https://safeweb.norton.com/)
- Stopbadware (https://www.stopbadware.org/clearinghouse/search/)
A well-trained workforce with knowledge of how hostile hackers often operate is necessary for an efficient online security plan. Most importantly, A mock phishing campaign can therefore assist the team in better comprehending how hackers can trick users into compromising critical information and taking precautions against it. Certainly, Cyberattacks on your company website will be less likely if you protect your staff from online crooks.
In conclusion, With the use of security awareness training, several security vulnerabilities can be quickly fixed. To clarify, A security team that has access to a training program can keep a full report on the weakest links in the security chain and strengthen them. Additionally, companies can then restrict access to these linkages or make them more resilient to attacks.










